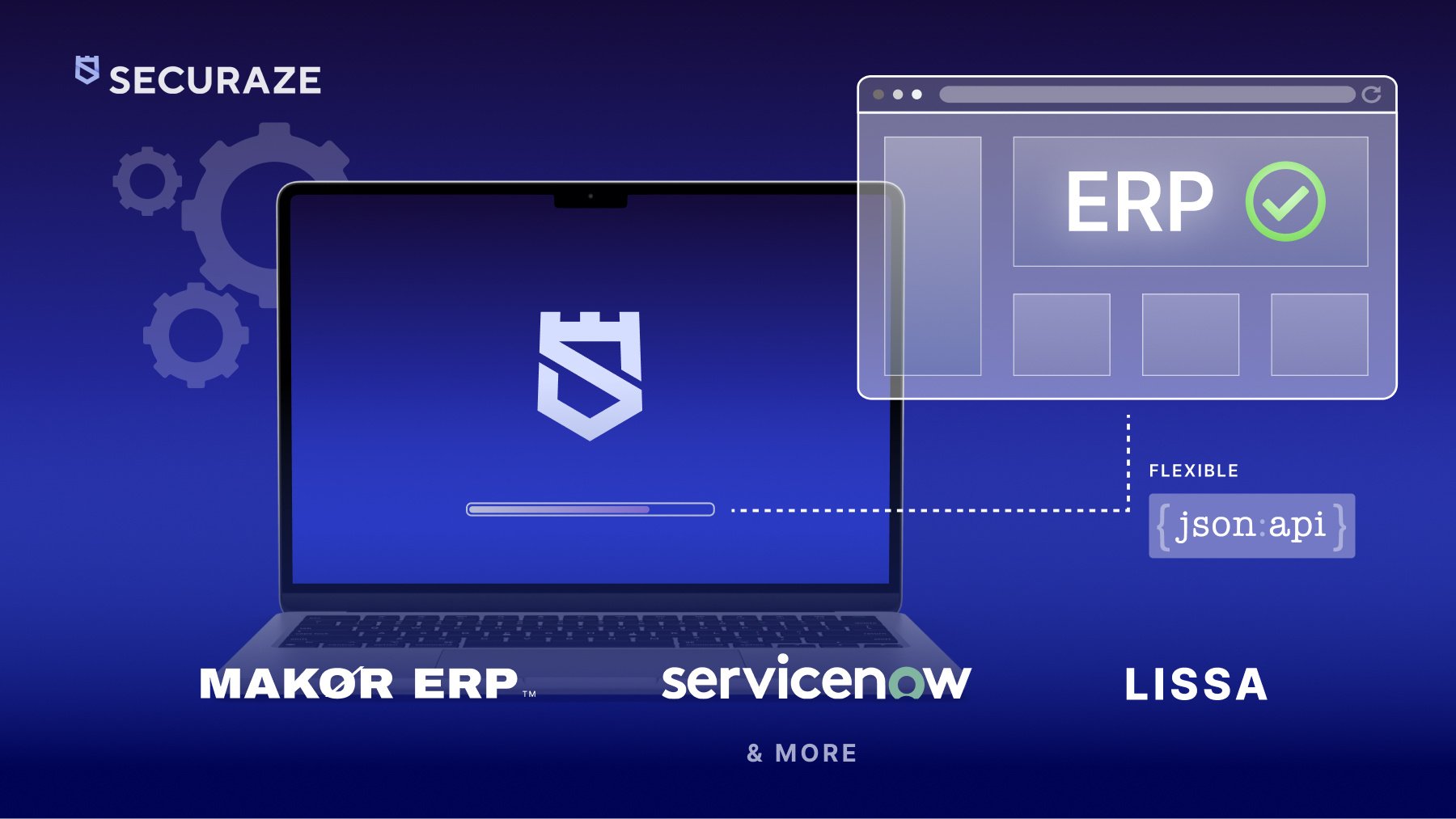
Seamless ERP Integration with Securaze: Streamline IT Asset Management with Dual-Endpoint Data Sync
In today’s fast-paced IT asset management industry, seamless data exchange between systems is crucial for efficiency, accuracy, and compliance. Securaze has been designed to integrate smoothly with external systems, particularly Enterprise Resource Planning (ERP) platforms, ensuring an automated and streamlined approach to handling asset data.




.png)